설치 매뉴얼
지니안 EDR 로그 전송 설정
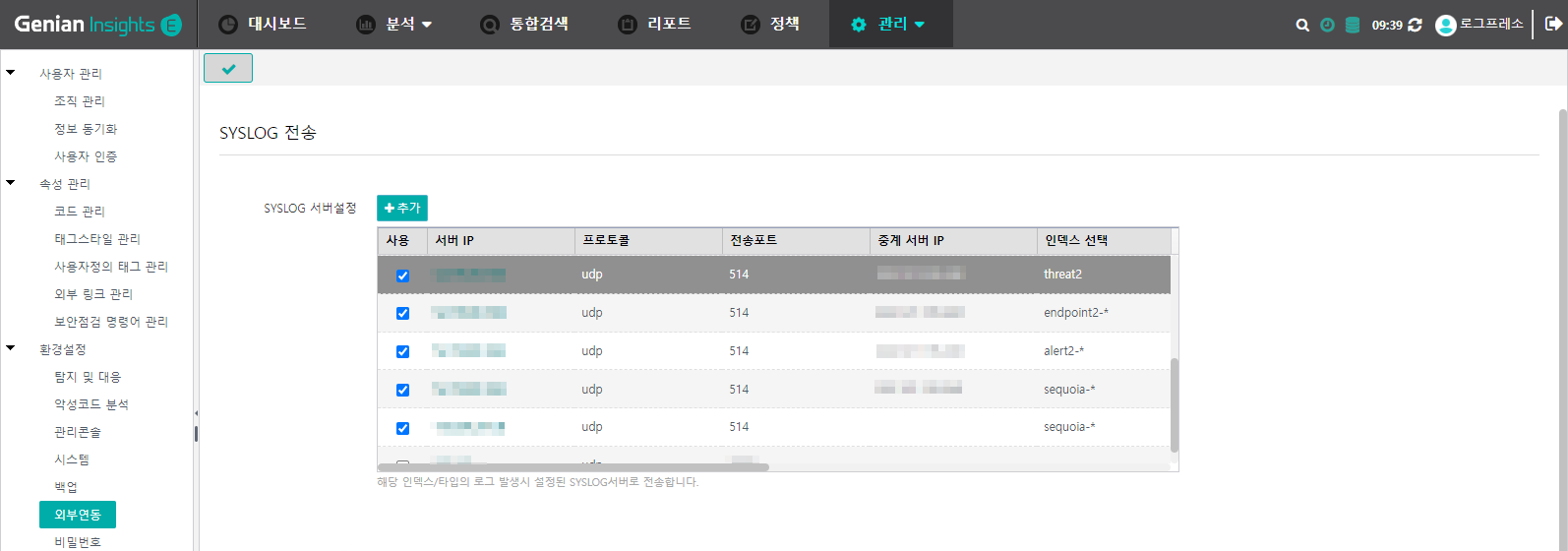
지니안 EDR 메뉴에서 관리 > 설정을 클릭하고, 왼쪽 메뉴에서 외부연동을 클릭합니다.
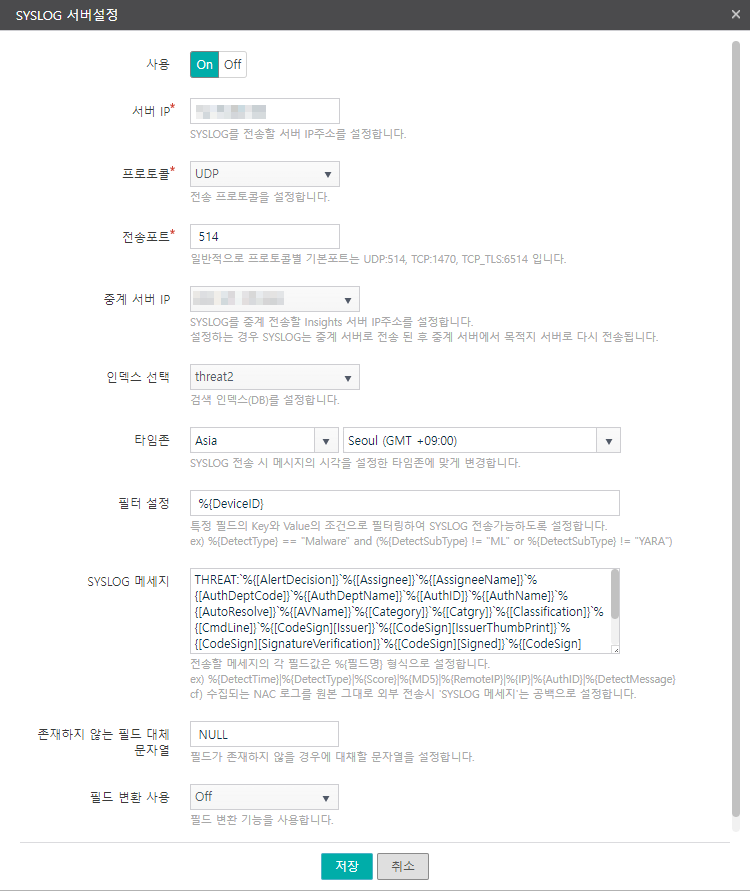
추가 버튼을 클릭하면 아래와 같은 대화상자가 표시됩니다.
아래 설정을 복사하여 4개의 SYSLOG 서버 설정을 추가합니다. 아래의 설정은 기본값이 아니며 지니안 EDR 로그 파싱 시 접두어와 필드 순서에 의존하기 때문에 반드시 아래 SYSLOG 메세지 설정을 적용해야 합니다.
threat2 인덱스
SYSLOG 메세지
THREAT:`%{[AlertDecision]}`%{[Assignee]}`%{[AssigneeName]}`%{[AuthDeptCode]}`%{[AuthDeptName]}`%{[AuthID]}`%{[AuthName]}`%{[AutoResolve]}`%{[AVName]}`%{[Category]}`%{[Catgry]}`%{[Classification]}`%{[CmdLine]}`%{[CodeSign][Issuer]}`%{[CodeSign][IssuerThumbPrint]}`%{[CodeSign][SignatureVerification]}`%{[CodeSign][Signed]}`%{[CodeSign][SigningDate]}`%{[CodeSign][Subject]}`%{[CodeSign][SubjectThumbPrint]}`%{[CodeSign][Type]}`%{[CollectServerID]}`%{[CollectTime]}`%{[Confidence]}`%{[CreateTime]}`%{[DeptCodePath]}`%{[DeptNamePath]}`%{[Details]}`%{[DetectID]}`%{[DetectKeyString]}`%{[DetectMessage]}`%{[DetectSubType]}`%{[DetectTime]}`%{[DetectType]}`%{[DeviceID]}`%{[Direction]}`%{[DNSName]}`%{[Domain]}`%{[EventSeq]}`%{[EventSubType]}`%{[EventTime]}`%{[EventType]}`%{[Feed]}`%{[FileName]}`%{[FileName2]}`%{[FilePath]}`%{[FilePath2]}`%{[FileSize]}`%{[FileType]}`%{[FirstTime]}`%{[FollowLink]}`%{[HostName]}`%{[Information][CategoryID]}`%{[Information][CategoryName]}`%{[Information][PathInfo]}`%{[Information][ProductName]}`%{[Information][SourceName]}`%{[Information][ThreatInfo]}`%{[Information][ThreatName]}`%{[IP]}`%{[IsKnown]}`%{[Level]}`%{[LocalIP]}`%{[LocalPort]}`%{[LogonID]}`%{[MAC]}`%{[MalwareKind]}`%{[MD5]}`%{[Memo]}`%{[MLLevel]}`%{[MLScore]}`%{[ModifyTime]}`%{[Occurred]}`%{[PathInfo]}`%{[PathInfo2]}`%{[PathKey]}`%{[PID]}`%{[Platform]}`%{[ProcGuid]}`%{[ProcName]}`%{[ProcPath]}`%{[ProcPathKey]}`%{[Protocol]}`%{[RemoteIP]}`%{[RemotePort]}`%{[Response]}`%{[ResponseInfo]}`%{[ResponseRule]}`%{[Result]}`%{[Rule]}`%{[RuleID]}`%{[Score]}`%{[SessionID]}`%{[SHA256]}`%{[SSDEEP]}`%{[State]}
endpoint2 인덱스
SYSLOG 메세지
ENDPOINT:`%{[Access]}`%{[AuthDeptCode]}`%{[AuthDeptName]}`%{[AuthID]}`%{[AuthName]}`%{[BusType]}`%{[BytesRecved]}`%{[BytesSent]}`%{[Catgry]}`%{[CheckFlag]}`%{[ChildPID]}`%{[ChildProcGuid]}`%{[CmdLine]}`%{[ConnCnt]}`%{[CreateTime]}`%{[CustomTag]}`%{[DetectKey]}`%{[DetectType]}`%{[DeviceID]}`%{[Direction]}`%{[DisconnCnt]}`%{[DisconnectFlag]}`%{[DNSName]}`%{[DNSRequest]}`%{[DNSResponse]}`%{[Domain]}`%{[DriveType]}`%{[DriveType2]}`%{[EventSeq]}`%{[EventSubType]}`%{[EventTime]}`%{[EventType]}`%{[ExitFlag]}`%{[ExitTime]}`%{[Ext]}`%{[Ext2]}`%{[FileAttr]}`%{[FileName]}`%{[FileName2]}`%{[FilePath]}`%{[FilePath2]}`%{[FileSize]}`%{[FileType]}`%{[FinalName]}`%{[HasDump]}`%{[HostName]}`%{[Important]}`%{[InflowSeq]}`%{[Info]}`%{[InfoTitle]}`%{[InjectionType]}`%{[IntegrityLevel]}`%{[InteractiveFlag]}`%{[IP]}`%{[IsSystem]}`%{[JsonInfo][DecodedCmdLine]}`%{[JsonInfo][WebTitle]}`%{[JsonInfo][WebURL]}`%{[JsonInfo][WindowText]}`%{[LastDisconnTime]}`%{[LocalIP]}`%{[LocalPort]}`%{[LogonID]}`%{[MD5]}`%{[ModifyTime]}`%{[offline]}`%{[ParentProcEventSeq]}`%{[ParentProcGuid]}`%{[ParentProcName]}`%{[PID]}`%{[PPID]}`%{[ProcGuid]}`%{[ProcName]}`%{[ProcPath]}`%{[ProcUserID]}`%{[Protocol]}`%{[RegDataSize]}`%{[RegDataType]}`%{[RegKeyPath]}`%{[RegNewKeyPath]}`%{[RegValue]}`%{[RegValueName]}`%{[RelatedEventSeq]}`%{[RelatedPID]}`%{[RelatedProcGuid]}`%{[RelatedProcName]}`%{[RelatedProcPath]}`%{[RemoteIP]}`%{[RemotePort]}`%{[ReqEventSeq]}`%{[ReqGuid]}`%{[ReqName]}`%{[ReqPID]}`%{[Result]}`%{[RuleID]}`%{[SerialNumber]}`%{[SessionID]}`%{[SHA256]}`%{[Tactic]}`%{[Tag]}`%{[TargetPID]}`%{[TargetProcGuid]}`%{[TargetProcName]}`%{[TargetProcPath]}`%{[Technique]}`%{[TrunkID]}`%{[Uncertain]}`%{[VolumeGuid]}`%{[VolumeType]}`%{[WindowClassName]}`%{[WindowText]}
alert2 인덱스
SYSLOG 메세지
ALERT:`%{[AuthDeptCode]}`%{[AuthDeptName]}`%{[AuthID]}`%{[AuthName]}`%{[AVName]}`%{[Catgry]}`%{[Classification]}`%{[CmdLine]}`%{[CodeSign][Issuer]}`%{[CodeSign][IssuerThumbPrint]}`%{[CodeSign][SignatureVerification]}`%{[CodeSign][Signed]}`%{[CodeSign][SigningDate]}`%{[CodeSign][Subject]}`%{[CodeSign][SubjectThumbPrint]}`%{[CodeSign][Type]}`%{[Confidence]}`%{[CreateTime]}`%{[DeptCodePath]}`%{[DeptNamePath]}`%{[Details]}`%{[DetectID]}`%{[DetectKeyString]}`%{[DetectMessage]}`%{[DetectSubType]}`%{[DetectTime]}`%{[DetectType]}`%{[DeviceID]}`%{[Direction]}`%{[DNSName]}`%{[Domain]}`%{[EventSeq]}`%{[EventSubType]}`%{[EventTime]}`%{[EventType]}`%{[Feed]}`%{[FileName]}`%{[FileName2]}`%{[FilePath]}`%{[FilePath2]}`%{[FileSize]}`%{[FileType]}`%{[FollowLink]}`%{[HostName]}`%{[Information][CategoryID]}`%{[Information][CategoryName]}`%{[Information][PathInfo]}`%{[Information][ProductName]}`%{[Information][SourceName]}`%{[Information][ThreatInfo]}`%{[Information][ThreatName]}`%{[IP]}`%{[IsKnown]}`%{[Level]}`%{[LocalIP]}`%{[LocalPort]}`%{[LogonID]}`%{[MAC]}`%{[MalwareKind]}`%{[MD5]}`%{[MLLevel]}`%{[MLScore]}`%{[ModifyTime]}`%{[PathInfo]}`%{[PathInfo2]}`%{[PathKey]}`%{[PID]}`%{[Platform]}`%{[ProcGuid]}`%{[ProcName]}`%{[ProcPath]}`%{[ProcPathKey]}`%{[Protocol]}`%{[RemoteIP]}`%{[RemotePort]}`%{[Response]}`%{[ResponseInfo]}`%{[ResponseRule]}`%{[Result]}`%{[RuleID]}`%{[Score]}`%{[SessionID]}`%{[SHA256]}`%{[SSDEEP]}`%{[SuspiciousInfo][Confidence]}`%{[SuspiciousInfo][FileName]}`%{[SuspiciousInfo][FilePath]}`%{[SuspiciousInfo][FileSize]}`%{[SuspiciousInfo][FileType]}`%{[SuspiciousInfo][MD5]}`%{[SuspiciousInfo][MLLevel]}`%{[SuspiciousInfo][MLScore]}`%{[SuspiciousInfo][SHA256]}`%{[SuspiciousInfo][SSDEEP]}`%{[SuspiciousInfo2][Confidence]}`%{[SuspiciousInfo2][FileName]}`%{[SuspiciousInfo2][FilePath]}`%{[SuspiciousInfo2][FileSize]}`%{[SuspiciousInfo2][FileType]}`%{[SuspiciousInfo2][MD5]}`%{[SuspiciousInfo2][MLLevel]}`%{[SuspiciousInfo2][MLScore]}`%{[SuspiciousInfo2][SHA256]}`%{[SuspiciousInfo2][SSDEEP]}`%{[SuspiciousInfo3][Confidence]}`%{[SuspiciousInfo3][FileName]}`%{[SuspiciousInfo3][FilePath]}`%{[SuspiciousInfo3][FileSize]}`%{[SuspiciousInfo3][FileType]}`%{[SuspiciousInfo3][MD5]}`%{[SuspiciousInfo3][MLLevel]}`%{[SuspiciousInfo3][MLScore]}`%{[SuspiciousInfo3][SHA256]}`%{[SuspiciousInfo3][SSDEEP]}`%{[ThreatID]}`%{[YaraRuleID]}`%{[YaraRuleName]}
sequoia 인덱스
SYSLOG 메세지
AUDIT:`%{[@timestamp]}`%{[actionStatusCode]}`%{[logAlertId]}`%{[logDetail]}`%{[logDeviceId]}`%{[logId]}`%{[logIdStr]}`%{[logIp]}`%{[logLinkID]}`%{[logLinkType]}`%{[logMac]}`%{[logMsg]}`%{[logThreatId]}`%{[logType]}`%{[logTypeStr]}`%{[logUserId]}`%{[logUserName]}
Note
지니안 EDR에 SYSLOG 서버 설정을 추가한 후 SYSLOG 서버 설정 목록 상단의 체크 버튼을 클릭하여 적용해야 반영됩니다.
로그프레소 수집기 설정
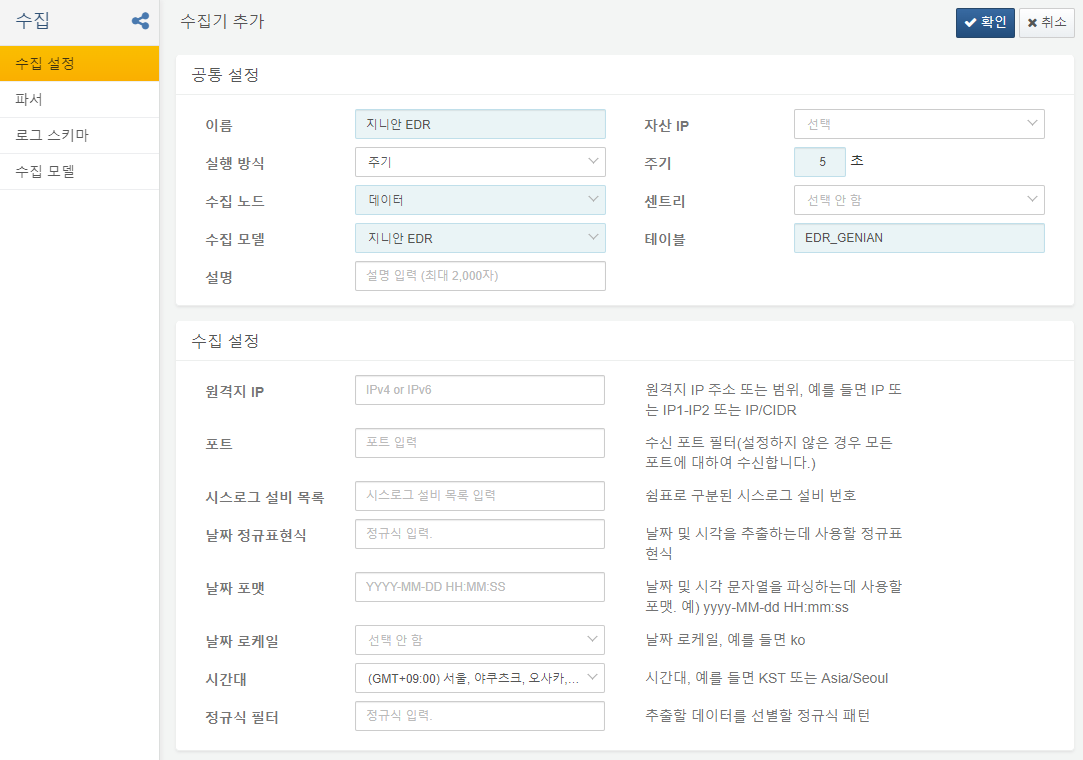
아래와 같이 설정하여 지니안 EDR 수집기를 추가하고 활성화합니다.
- 수집 모델: 지니안 EDR
- 테이블: EDR_GENIAN
- 테이블 이름 변경 시 데이터셋의 테이블 이름도 변경하세요.
- 원격지 IP: 지니안 EDR 서버 또는 중계 서버의 IP 주소