Install Guide
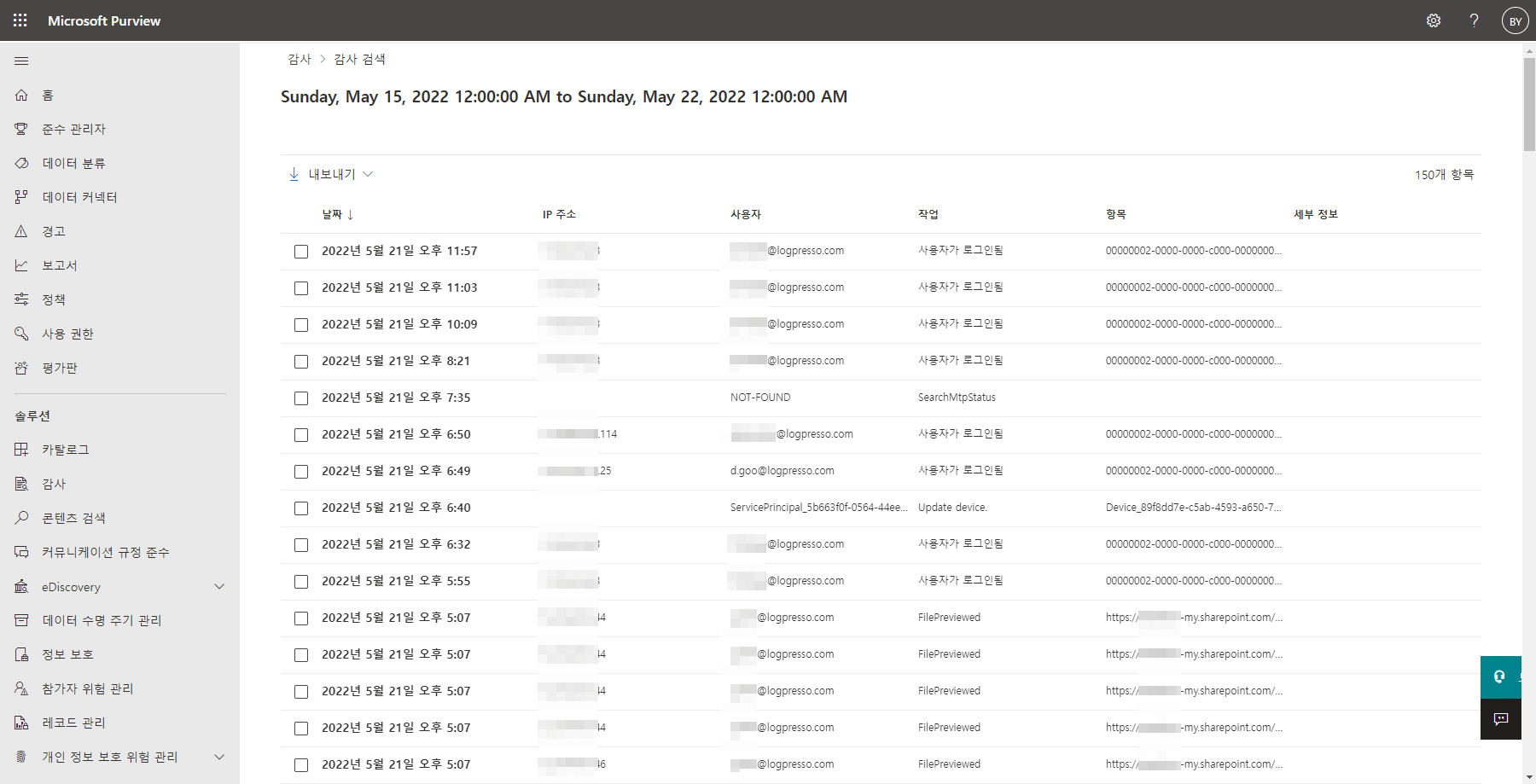
Microsoft Office 365 is a subscription-based office suite that includes Word, Excel, PowerPoint, OneNote, and OneDrive. It also supports compliance management through Microsoft Purview. For example, Purview allows for searching audit logs as shown below:
The data in the Security & Compliance Center is retained for only 7 days and the built-in audit log search feature makes data analysis challenging. For more effective analysis, it is recommended to integrate Microsoft Office 365 with the Logpresso platform.
Set Up Azure Portal
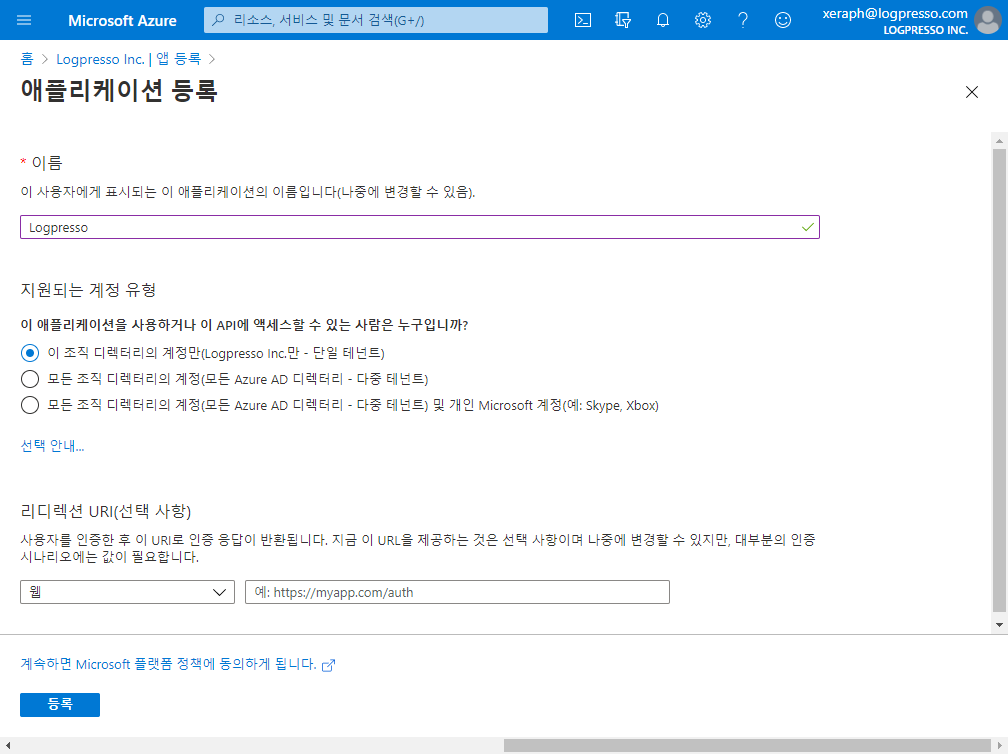
After signing in to the Azure portal, navigate to Azure Active Directory to access the application register screen. From here, register a new application as shown below:
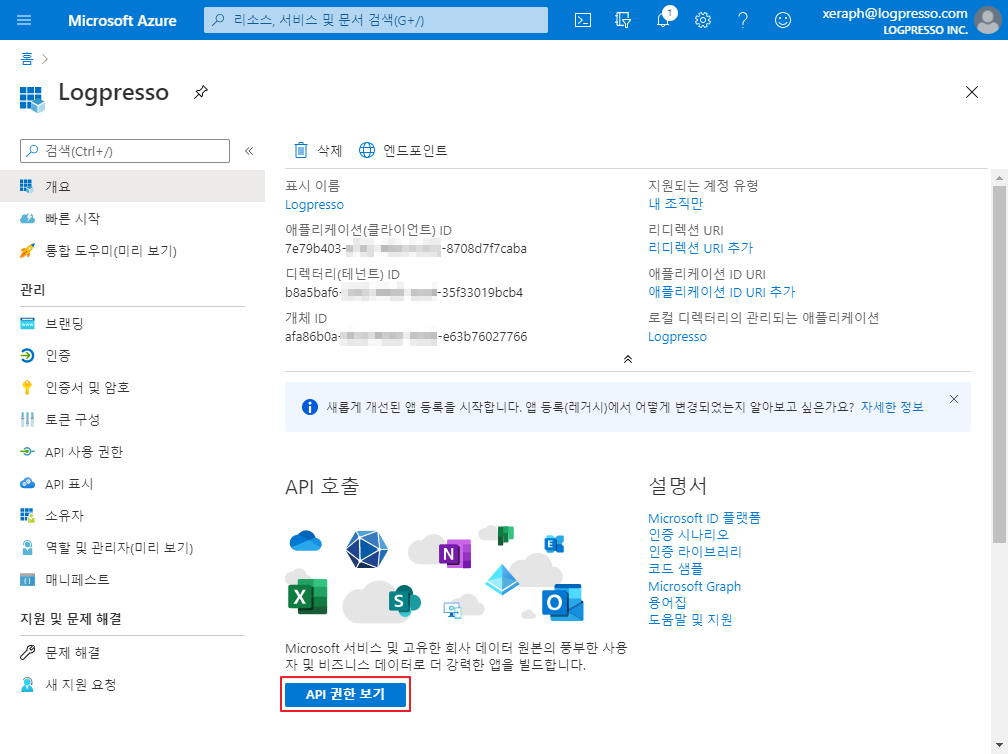
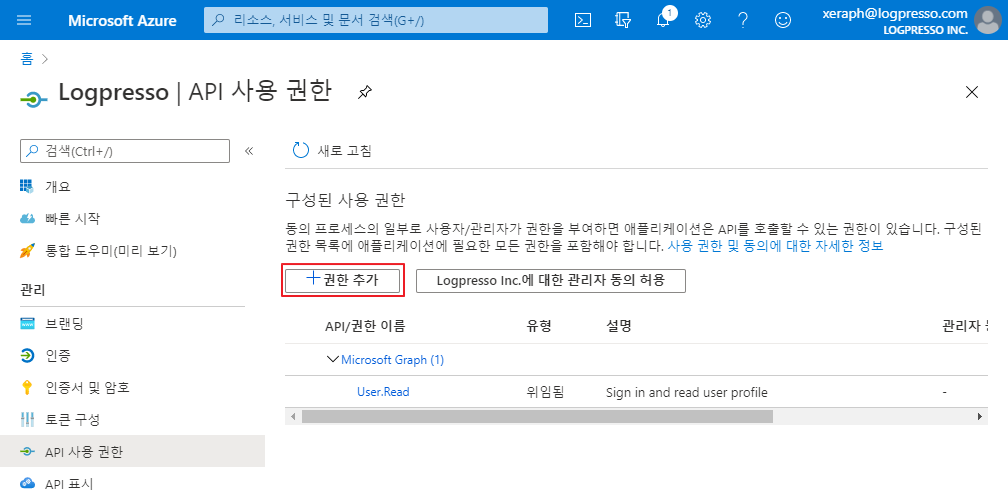
Once the application is created, proceed to the API Permissions screen:
Click the Add Permission button:
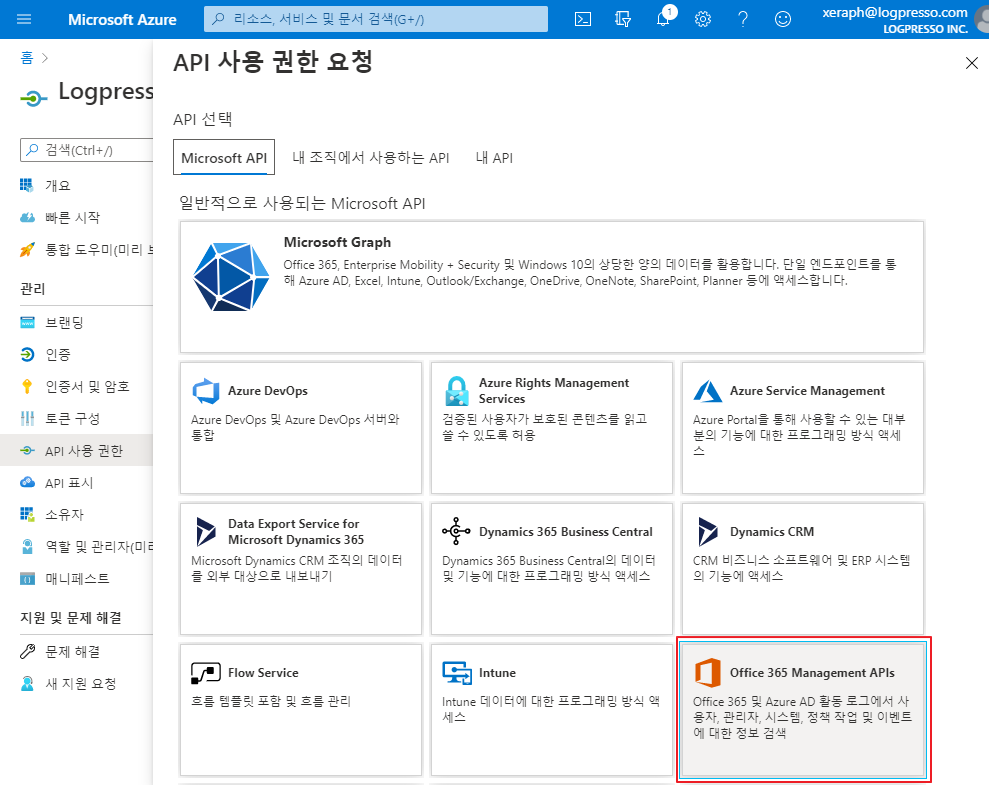
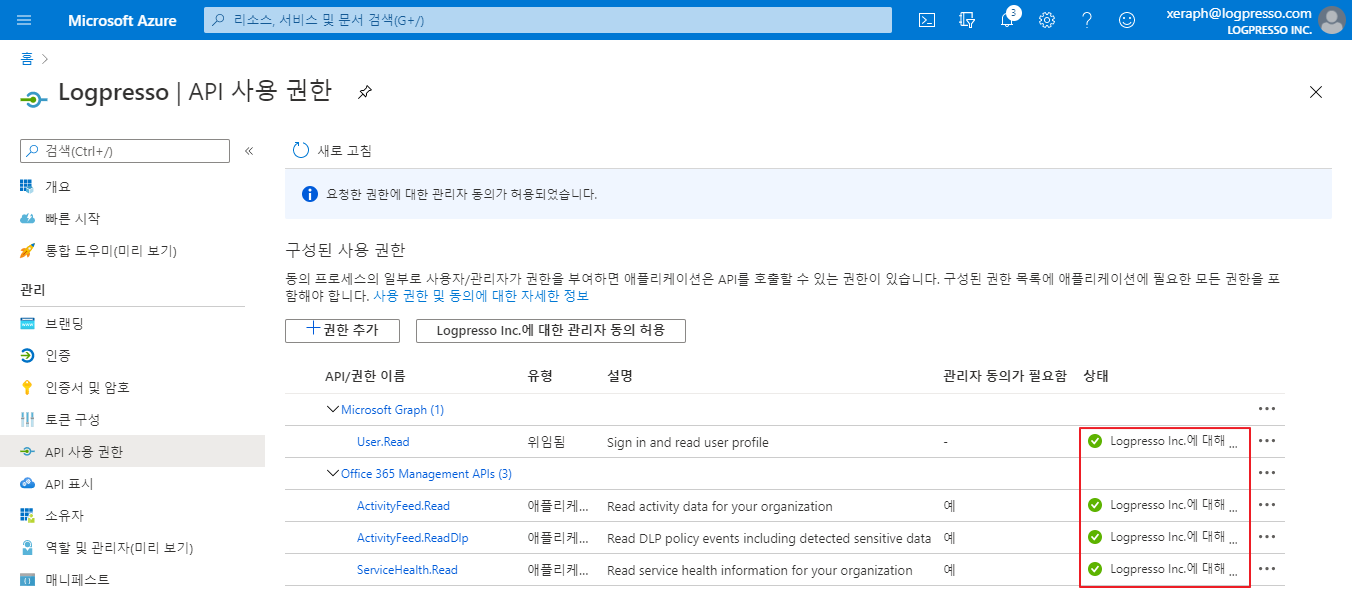
In the list of permissions, select Office 365 Management APIs:
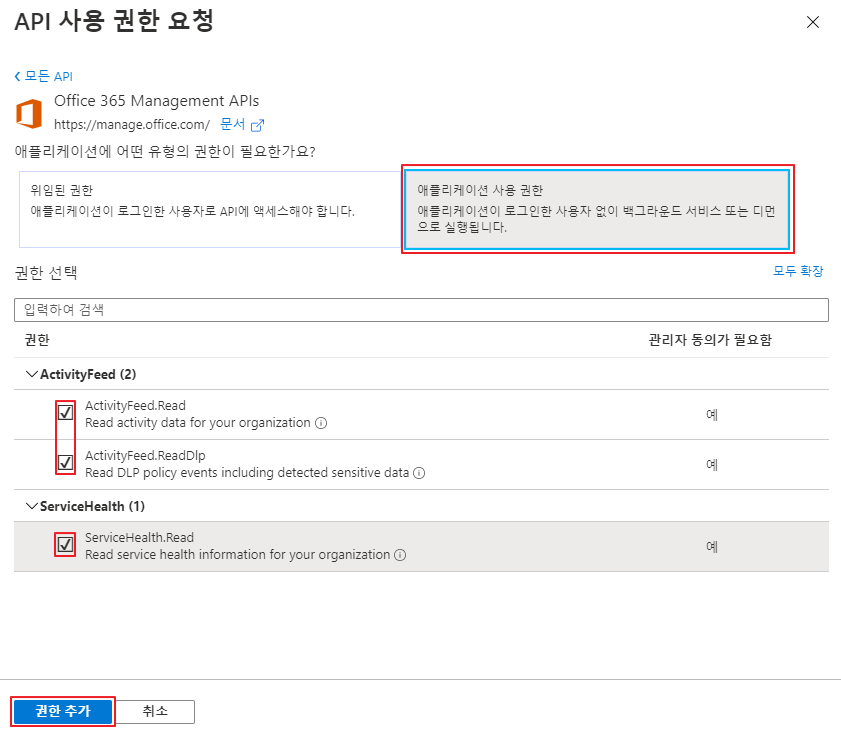
Choose the Application Permissions type, check and add all permissions:
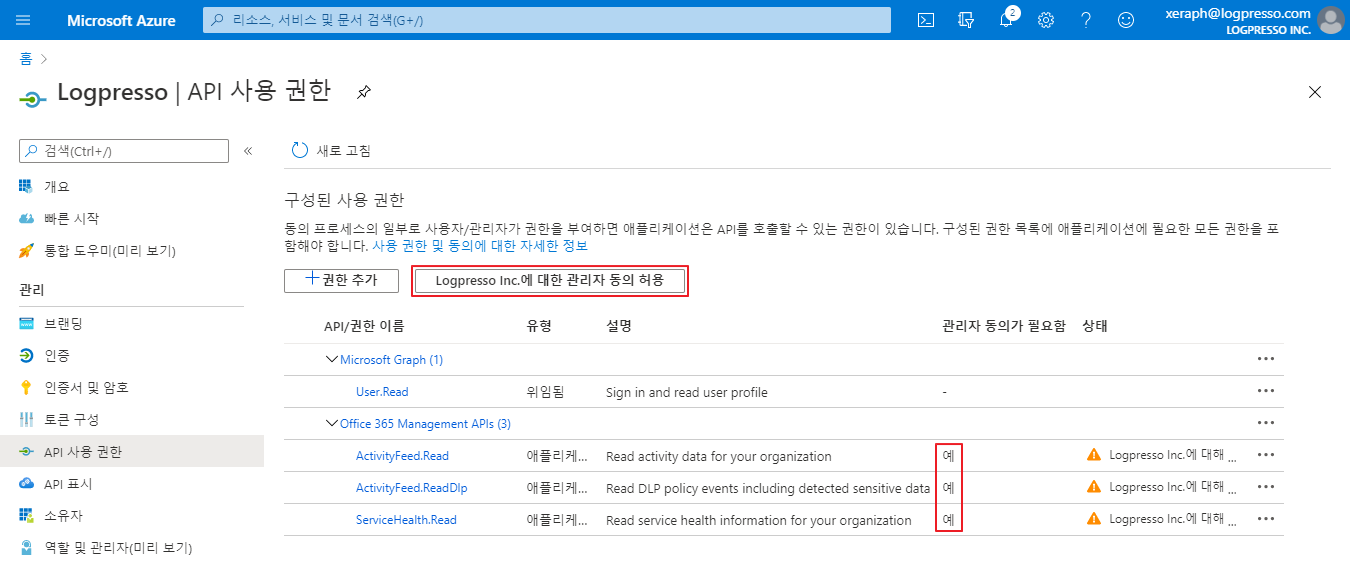
After adding the permission, an administrator must approve it. Ensure that Admin consent required is set to Yes, then click the Grant admin consent button:
Once approved, the status will change to Granted:
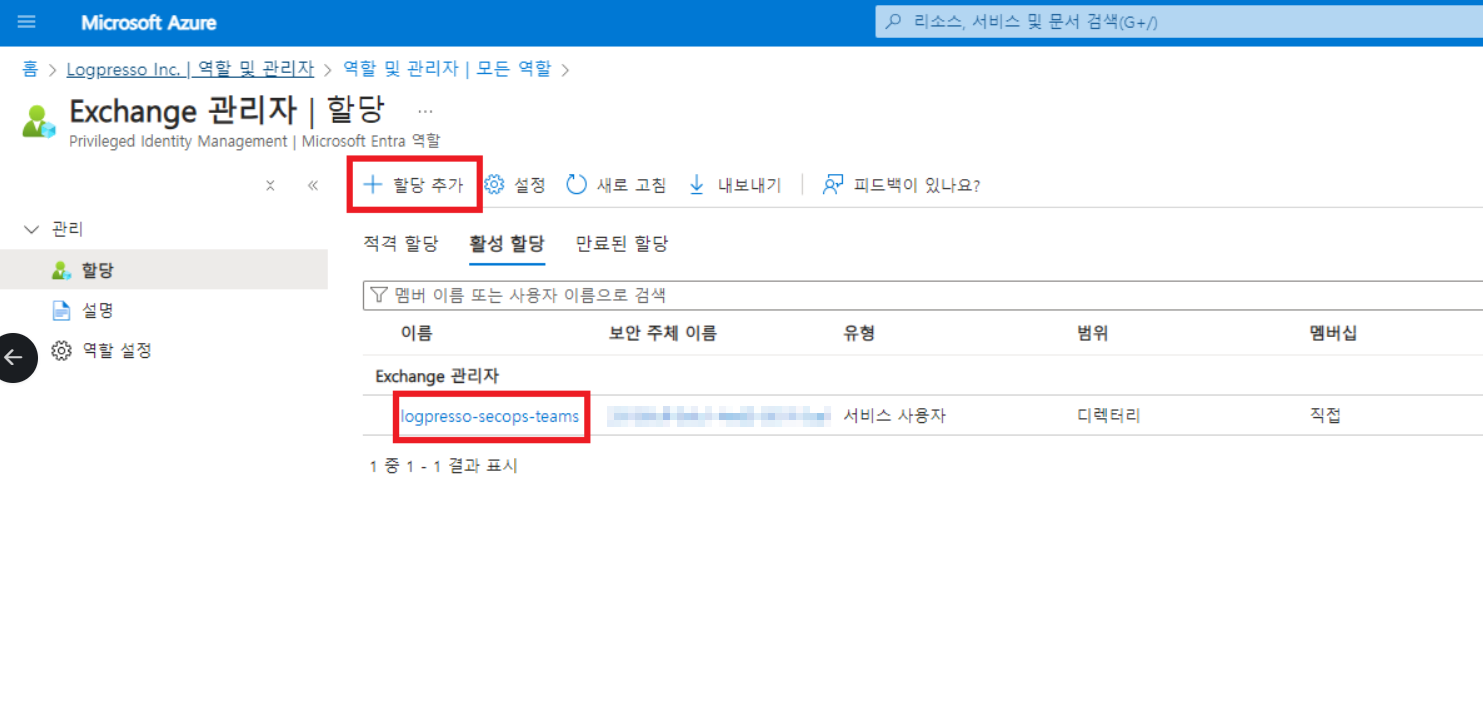
To collect mail flow data, the created application must be assigned one of the following administrative roles (navigate to Entra ID > Roles and Administrators):
- Global reader
- Security reader
- Exchange Administrator
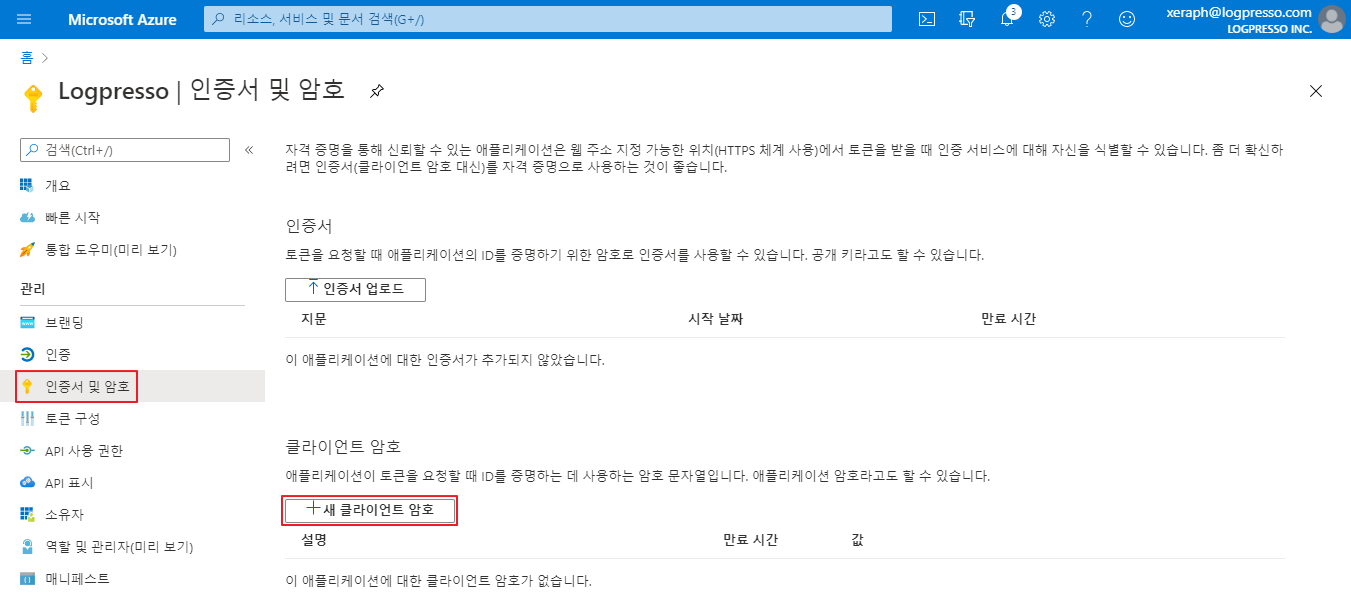
Next, generate a new client password by navigating to Certificates and Passwords and clicking on New Client Password:
Note that the generated client secret cannot be retrieved after leaving the screen. Make sure to copy and save it. If you accidentally leave the screen, delete the secret and generate a new one.
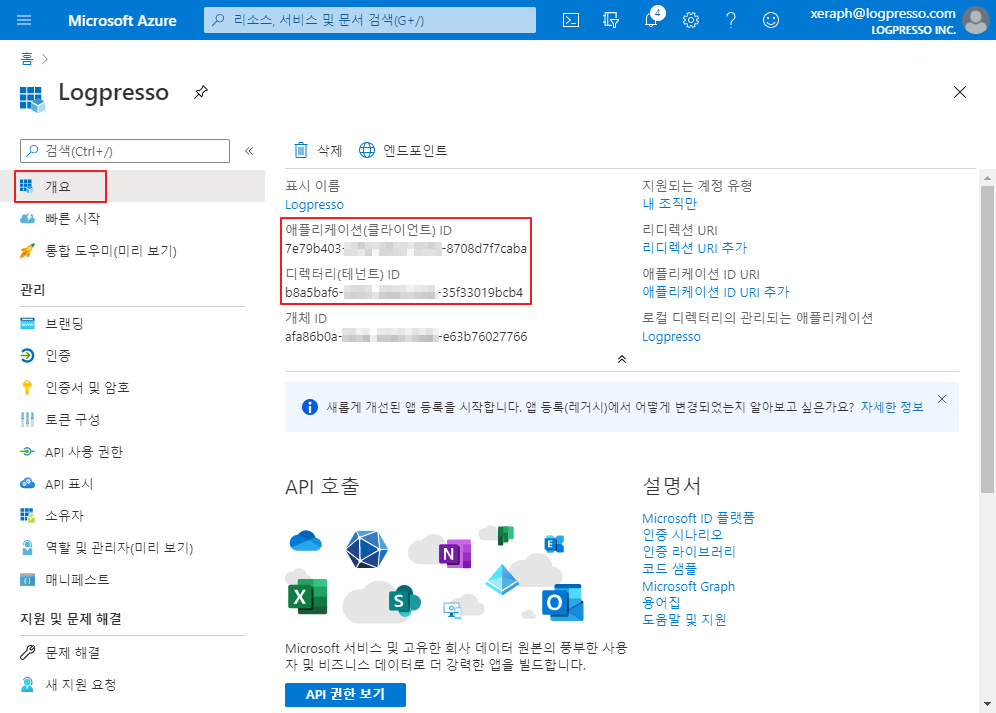
Finally, on the Overview page, you can find the Tenant ID, Client ID, and Client Secret:
Firewall Policy
To use the extended query commands and logger, your firewall policy must allow the Logpresso server to access the following URLs:
- https://manage.office.com
- https://login.microsoftonline.com
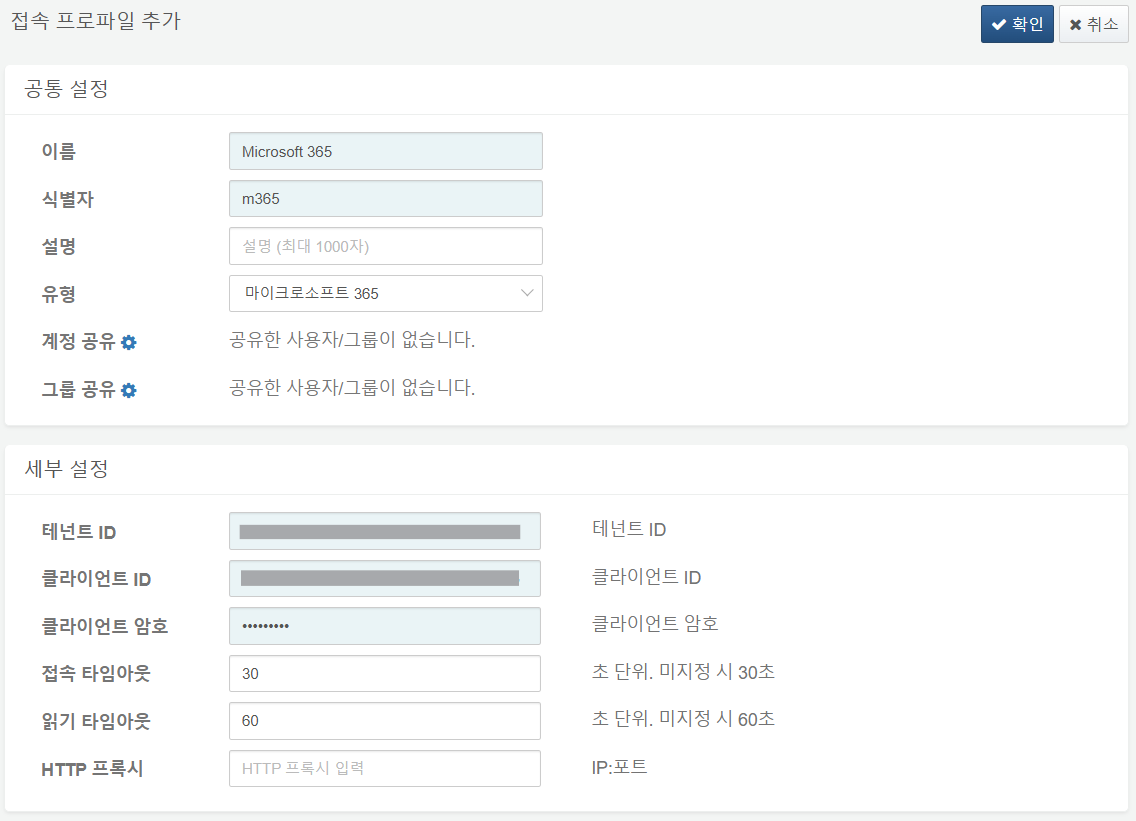
Set Up Connect Profile
Enter the three pieces of information you obtained from the overview screen into the Logpresso connect profile. If you are using an HTTP proxy, be sure to include the proxy settings as well.
Set Up Logpresso Logger
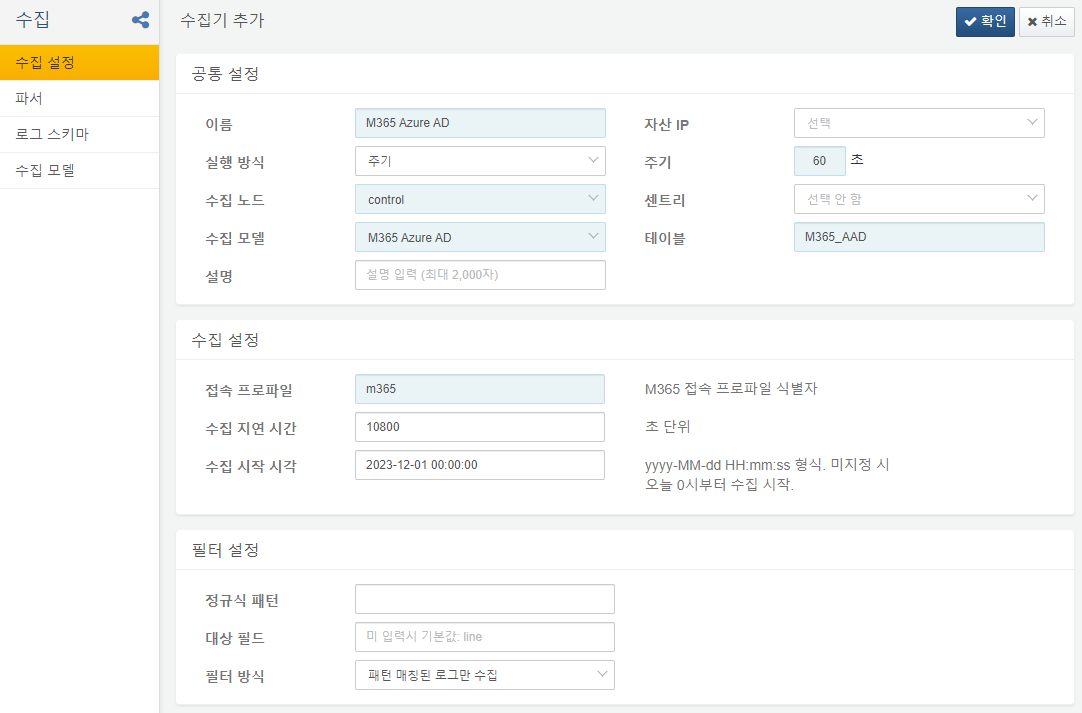
Azure AD Logger
Azure AD Logger saves the Microsoft 365 Azure Active Directory audit logs in the M365_AAD table.
Connect Profile: Microsoft 365 connection profile identifier
Collection Delay Time: 10800 seconds. If you collect without accounting for a time delay, you may miss audit logs written later, leading to potential data loss. Microsoft 365 audit logs can experience an average delay of 30 minutes and may take up to 3 hours to appear.
Collection Start Time: When to begin collecting logs using the format yyyy-MM-dd HH:mm:ss. Note that only logs up to 7 days old are available.
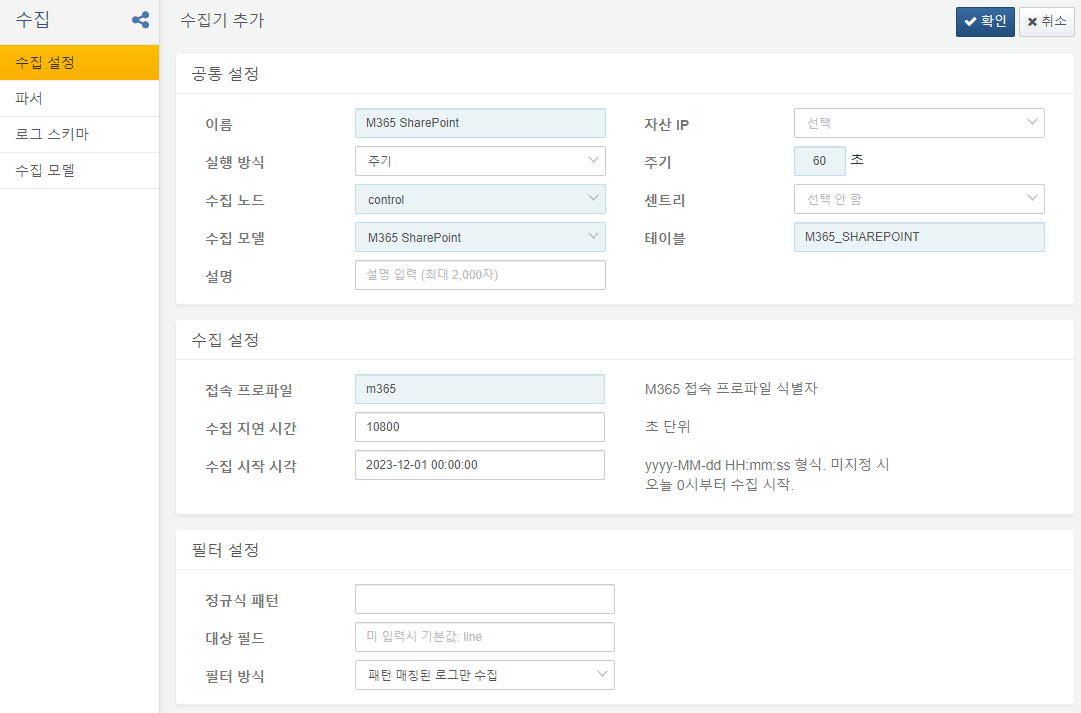
SharePoint Logger
SharePoint Logger saves the Microsoft 365 SharePoint and OneDrive audit logs in the M365_SHAREPOINT table.
Connect Profile: Microsoft 365 connection profile identifier
Collection Delay Time: 10800 seconds. If you collect without accounting for a time delay, you may miss audit logs written later, leading to potential data loss. Microsoft 365 audit logs can experience an average delay of 30 minutes and may take up to 3 hours to appear.
Collection Start Time: When to begin collecting logs using the format yyyy-MM-dd HH:mm:ss. Note that only logs up to 7 days old are available.
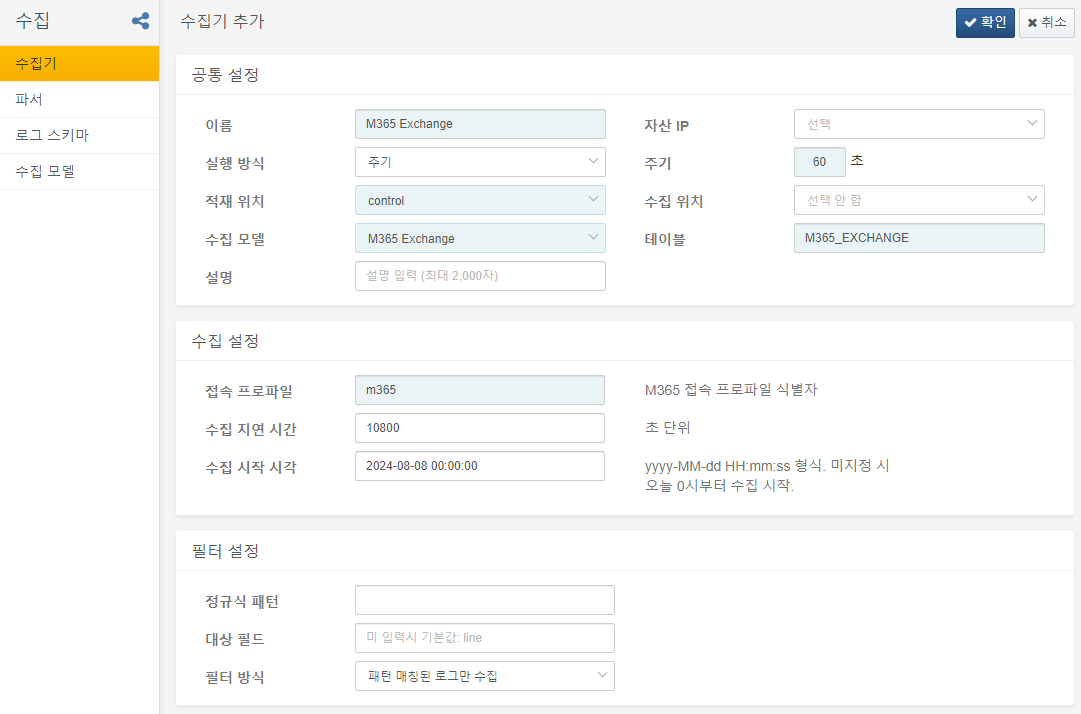
Exchange Logger
Exchange Logger saves the Microsoft 365 audit logs in the `M365_EXCHANGE table.
Connect Profile: Microsoft 365 connection profile identifier
Collection Delay Time: 10800 seconds. If you collect without accounting for a time delay, you may miss audit logs written later, leading to potential data loss. Microsoft 365 audit logs can experience an average delay of 30 minutes and may take up to 3 hours to appear.
Collection Start Time: When to begin collecting logs using the format yyyy-MM-dd HH:mm:ss. Note that only logs up to 7 days old are available.
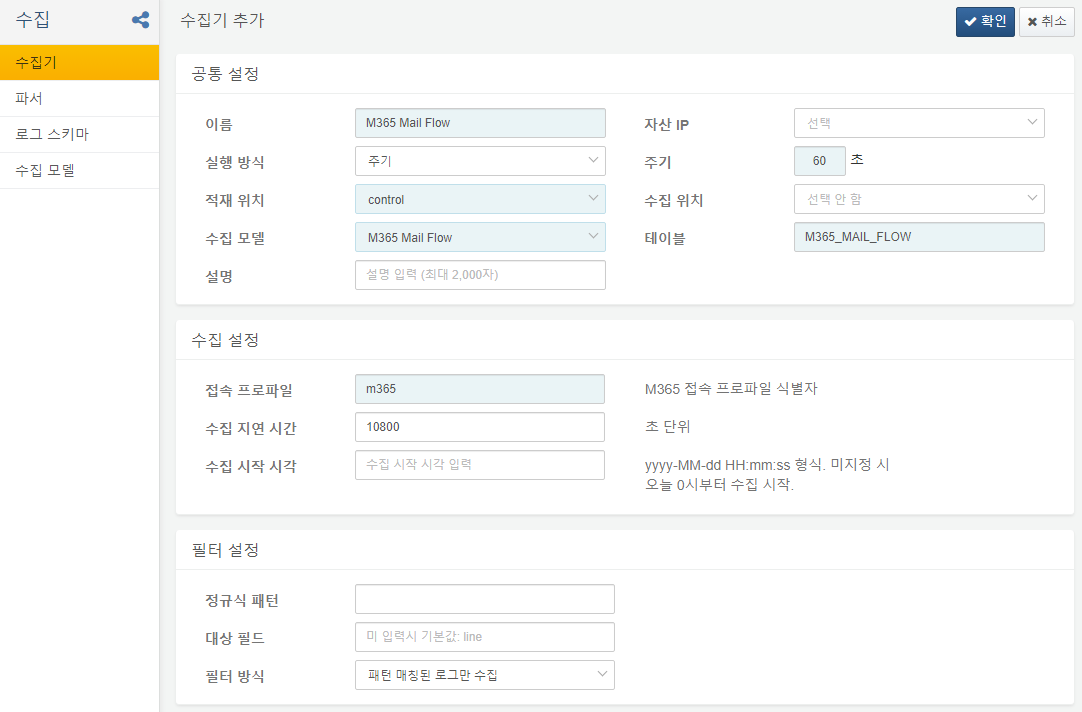
Mailflow data Logger
Mailflow data Logger saves the Microsoft 365 mailflow audit logs in the M365_MAIL_FLOW table.
Connect Profile: Microsoft 365 connection profile identifier
Collection Delay Time: 10800 seconds. If you collect without accounting for a time delay, you may miss audit logs written later, leading to potential data loss. Microsoft 365 audit logs can experience an average delay of 30 minutes and may take up to 3 hours to appear.
Collection Start Time: When to begin collecting logs using the format yyyy-MM-dd HH:mm:ss. Note that only logs up to 7 days old are available.
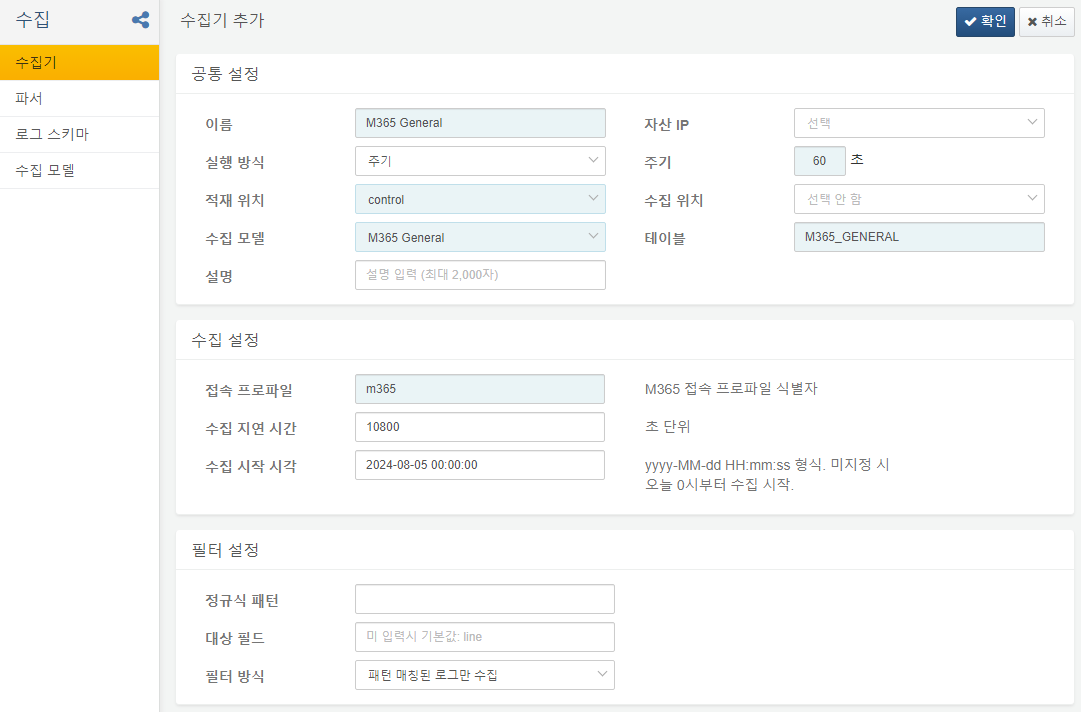
General Audit Log Logger
General Audit Log Logger saves the Microsoft 365 general audit logs in the M365_GENERAL table.
Connect Profile: Microsoft 365 connection profile identifier
Collection Delay Time: 10800 seconds. If you collect without accounting for a time delay, you may miss audit logs written later, leading to potential data loss. Microsoft 365 audit logs can experience an average delay of 30 minutes and may take up to 3 hours to appear.
Collection Start Time: When to begin collecting logs using the format yyyy-MM-dd HH:mm:ss. Note that only logs up to 7 days old are available.