Install Guide
Genian EDR Log Transmission Setup
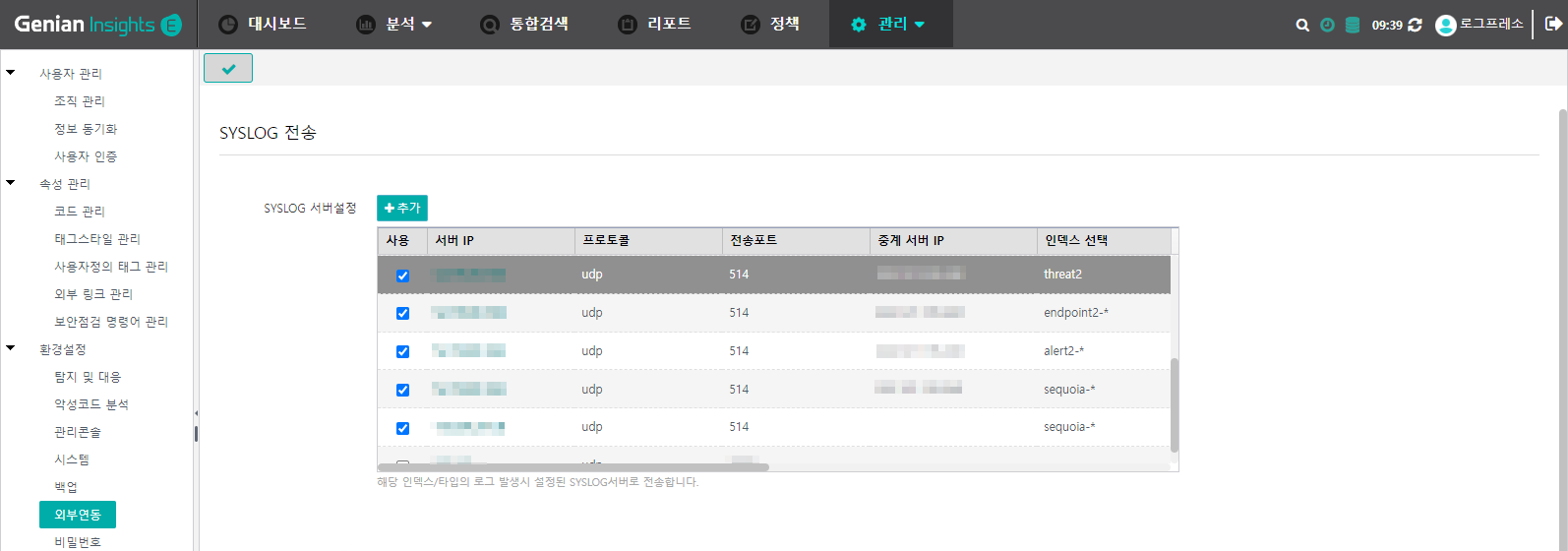
In the Genian EDR menu, navigate to Management > Settings and then select External Integration from the left menu.
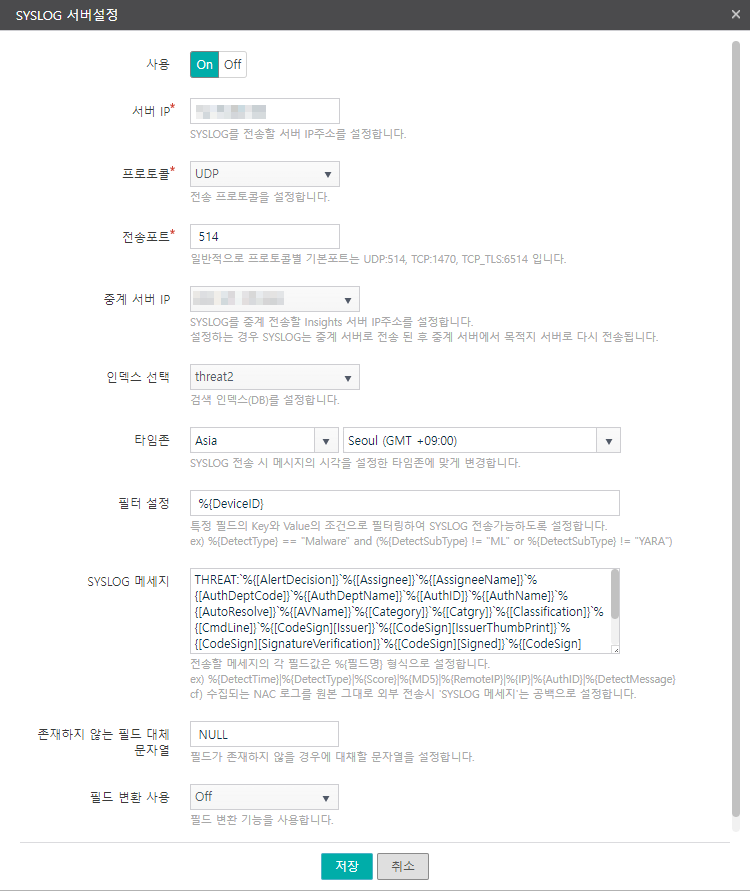
Click the Add button to display the following dialog.
Copy and add the following settings for 4 SYSLOG servers. These settings are not the defaults, and since Genian EDR log parsing depends on the prefix and field order, the following SYSLOG message settings must be applied.
threat2 Index
SYSLOG message:
THREAT:`%{[AlertDecision]}`%{[Assignee]}`%{[AssigneeName]}`%{[AuthDeptCode]}`%{[AuthDeptName]}`%{[AuthID]}`%{[AuthName]}`%{[AutoResolve]}`%{[AVName]}`%{[Category]}`%{[Catgry]}`%{[Classification]}`%{[CmdLine]}`%{[CodeSign][Issuer]}`%{[CodeSign][IssuerThumbPrint]}`%{[CodeSign][SignatureVerification]}`%{[CodeSign][Signed]}`%{[CodeSign][SigningDate]}`%{[CodeSign][Subject]}`%{[CodeSign][SubjectThumbPrint]}`%{[CodeSign][Type]}`%{[CollectServerID]}`%{[CollectTime]}`%{[Confidence]}`%{[CreateTime]}`%{[DeptCodePath]}`%{[DeptNamePath]}`%{[Details]}`%{[DetectID]}`%{[DetectKeyString]}`%{[DetectMessage]}`%{[DetectSubType]}`%{[DetectTime]}`%{[DetectType]}`%{[DeviceID]}`%{[Direction]}`%{[DNSName]}`%{[Domain]}`%{[EventSeq]}`%{[EventSubType]}`%{[EventTime]}`%{[EventType]}`%{[Feed]}`%{[FileName]}`%{[FileName2]}`%{[FilePath]}`%{[FilePath2]}`%{[FileSize]}`%{[FileType]}`%{[FirstTime]}`%{[FollowLink]}`%{[HostName]}`%{[Information][CategoryID]}`%{[Information][CategoryName]}`%{[Information][PathInfo]}`%{[Information][ProductName]}`%{[Information][SourceName]}`%{[Information][ThreatInfo]}`%{[Information][ThreatName]}`%{[IP]}`%{[IsKnown]}`%{[Level]}`%{[LocalIP]}`%{[LocalPort]}`%{[LogonID]}`%{[MAC]}`%{[MalwareKind]}`%{[MD5]}`%{[Memo]}`%{[MLLevel]}`%{[MLScore]}`%{[ModifyTime]}`%{[Occurred]}`%{[PathInfo]}`%{[PathInfo2]}`%{[PathKey]}`%{[PID]}`%{[Platform]}`%{[ProcGuid]}`%{[ProcName]}`%{[ProcPath]}`%{[ProcPathKey]}`%{[Protocol]}`%{[RemoteIP]}`%{[RemotePort]}`%{[Response]}`%{[ResponseInfo]}`%{[ResponseRule]}`%{[Result]}`%{[Rule]}`%{[RuleID]}`%{[Score]}`%{[SessionID]}`%{[SHA256]}`%{[SSDEEP]}`%{[State]}
endpoint2 Index
SYSLOG message
ENDPOINT:`%{[Access]}`%{[AuthDeptCode]}`%{[AuthDeptName]}`%{[AuthID]}`%{[AuthName]}`%{[BusType]}`%{[BytesRecved]}`%{[BytesSent]}`%{[Catgry]}`%{[CheckFlag]}`%{[ChildPID]}`%{[ChildProcGuid]}`%{[CmdLine]}`%{[ConnCnt]}`%{[CreateTime]}`%{[CustomTag]}`%{[DetectKey]}`%{[DetectType]}`%{[DeviceID]}`%{[Direction]}`%{[DisconnCnt]}`%{[DisconnectFlag]}`%{[DNSName]}`%{[DNSRequest]}`%{[DNSResponse]}`%{[Domain]}`%{[DriveType]}`%{[DriveType2]}`%{[EventSeq]}`%{[EventSubType]}`%{[EventTime]}`%{[EventType]}`%{[ExitFlag]}`%{[ExitTime]}`%{[Ext]}`%{[Ext2]}`%{[FileAttr]}`%{[FileName]}`%{[FileName2]}`%{[FilePath]}`%{[FilePath2]}`%{[FileSize]}`%{[FileType]}`%{[FinalName]}`%{[HasDump]}`%{[HostName]}`%{[Important]}`%{[InflowSeq]}`%{[Info]}`%{[InfoTitle]}`%{[InjectionType]}`%{[IntegrityLevel]}`%{[InteractiveFlag]}`%{[IP]}`%{[IsSystem]}`%{[JsonInfo][DecodedCmdLine]}`%{[JsonInfo][WebTitle]}`%{[JsonInfo][WebURL]}`%{[JsonInfo][WindowText]}`%{[LastDisconnTime]}`%{[LocalIP]}`%{[LocalPort]}`%{[LogonID]}`%{[MD5]}`%{[ModifyTime]}`%{[offline]}`%{[ParentProcEventSeq]}`%{[ParentProcGuid]}`%{[ParentProcName]}`%{[PID]}`%{[PPID]}`%{[ProcGuid]}`%{[ProcName]}`%{[ProcPath]}`%{[ProcUserID]}`%{[Protocol]}`%{[RegDataSize]}`%{[RegDataType]}`%{[RegKeyPath]}`%{[RegNewKeyPath]}`%{[RegValue]}`%{[RegValueName]}`%{[RelatedEventSeq]}`%{[RelatedPID]}`%{[RelatedProcGuid]}`%{[RelatedProcName]}`%{[RelatedProcPath]}`%{[RemoteIP]}`%{[RemotePort]}`%{[ReqEventSeq]}`%{[ReqGuid]}`%{[ReqName]}`%{[ReqPID]}`%{[Result]}`%{[RuleID]}`%{[SerialNumber]}`%{[SessionID]}`%{[SHA256]}`%{[Tactic]}`%{[Tag]}`%{[TargetPID]}`%{[TargetProcGuid]}`%{[TargetProcName]}`%{[TargetProcPath]}`%{[Technique]}`%{[TrunkID]}`%{[Uncertain]}`%{[VolumeGuid]}`%{[VolumeType]}`%{[WindowClassName]}`%{[WindowText]}
alert2 Index
SYSLOG message
ALERT:`%{[AuthDeptCode]}`%{[AuthDeptName]}`%{[AuthID]}`%{[AuthName]}`%{[AVName]}`%{[Catgry]}`%{[Classification]}`%{[CmdLine]}`%{[CodeSign][Issuer]}`%{[CodeSign][IssuerThumbPrint]}`%{[CodeSign][SignatureVerification]}`%{[CodeSign][Signed]}`%{[CodeSign][SigningDate]}`%{[CodeSign][Subject]}`%{[CodeSign][SubjectThumbPrint]}`%{[CodeSign][Type]}`%{[Confidence]}`%{[CreateTime]}`%{[DeptCodePath]}`%{[DeptNamePath]}`%{[Details]}`%{[DetectID]}`%{[DetectKeyString]}`%{[DetectMessage]}`%{[DetectSubType]}`%{[DetectTime]}`%{[DetectType]}`%{[DeviceID]}`%{[Direction]}`%{[DNSName]}`%{[Domain]}`%{[EventSeq]}`%{[EventSubType]}`%{[EventTime]}`%{[EventType]}`%{[Feed]}`%{[FileName]}`%{[FileName2]}`%{[FilePath]}`%{[FilePath2]}`%{[FileSize]}`%{[FileType]}`%{[FollowLink]}`%{[HostName]}`%{[Information][CategoryID]}`%{[Information][CategoryName]}`%{[Information][PathInfo]}`%{[Information][ProductName]}`%{[Information][SourceName]}`%{[Information][ThreatInfo]}`%{[Information][ThreatName]}`%{[IP]}`%{[IsKnown]}`%{[Level]}`%{[LocalIP]}`%{[LocalPort]}`%{[LogonID]}`%{[MAC]}`%{[MalwareKind]}`%{[MD5]}`%{[MLLevel]}`%{[MLScore]}`%{[ModifyTime]}`%{[PathInfo]}`%{[PathInfo2]}`%{[PathKey]}`%{[PID]}`%{[Platform]}`%{[ProcGuid]}`%{[ProcName]}`%{[ProcPath]}`%{[ProcPathKey]}`%{[Protocol]}`%{[RemoteIP]}`%{[RemotePort]}`%{[Response]}`%{[ResponseInfo]}`%{[ResponseRule]}`%{[Result]}`%{[RuleID]}`%{[Score]}`%{[SessionID]}`%{[SHA256]}`%{[SSDEEP]}`%{[SuspiciousInfo][Confidence]}`%{[SuspiciousInfo][FileName]}`%{[SuspiciousInfo][FilePath]}`%{[SuspiciousInfo][FileSize]}`%{[SuspiciousInfo][FileType]}`%{[SuspiciousInfo][MD5]}`%{[SuspiciousInfo][MLLevel]}`%{[SuspiciousInfo][MLScore]}`%{[SuspiciousInfo][SHA256]}`%{[SuspiciousInfo][SSDEEP]}`%{[SuspiciousInfo2][Confidence]}`%{[SuspiciousInfo2][FileName]}`%{[SuspiciousInfo2][FilePath]}`%{[SuspiciousInfo2][FileSize]}`%{[SuspiciousInfo2][FileType]}`%{[SuspiciousInfo2][MD5]}`%{[SuspiciousInfo2][MLLevel]}`%{[SuspiciousInfo2][MLScore]}`%{[SuspiciousInfo2][SHA256]}`%{[SuspiciousInfo2][SSDEEP]}`%{[SuspiciousInfo3][Confidence]}`%{[SuspiciousInfo3][FileName]}`%{[SuspiciousInfo3][FilePath]}`%{[SuspiciousInfo3][FileSize]}`%{[SuspiciousInfo3][FileType]}`%{[SuspiciousInfo3][MD5]}`%{[SuspiciousInfo3][MLLevel]}`%{[SuspiciousInfo3][MLScore]}`%{[SuspiciousInfo3][SHA256]}`%{[SuspiciousInfo3][SSDEEP]}`%{[ThreatID]}`%{[YaraRuleID]}`%{[YaraRuleName]}
sequoia Index
SYSLOG message
AUDIT:`%{[@timestamp]}`%{[actionStatusCode]}`%{[logAlertId]}`%{[logDetail]}`%{[logDeviceId]}`%{[logId]}`%{[logIdStr]}`%{[logIp]}`%{[logLinkID]}`%{[logLinkType]}`%{[logMac]}`%{[logMsg]}`%{[logThreatId]}`%{[logType]}`%{[logTypeStr]}`%{[logUserId]}`%{[logUserName]}
Note
After configuring SYSLOG server settings in Genian EDR, make sure to click the check button at the top of the SYSLOG server settings list to apply the changes.
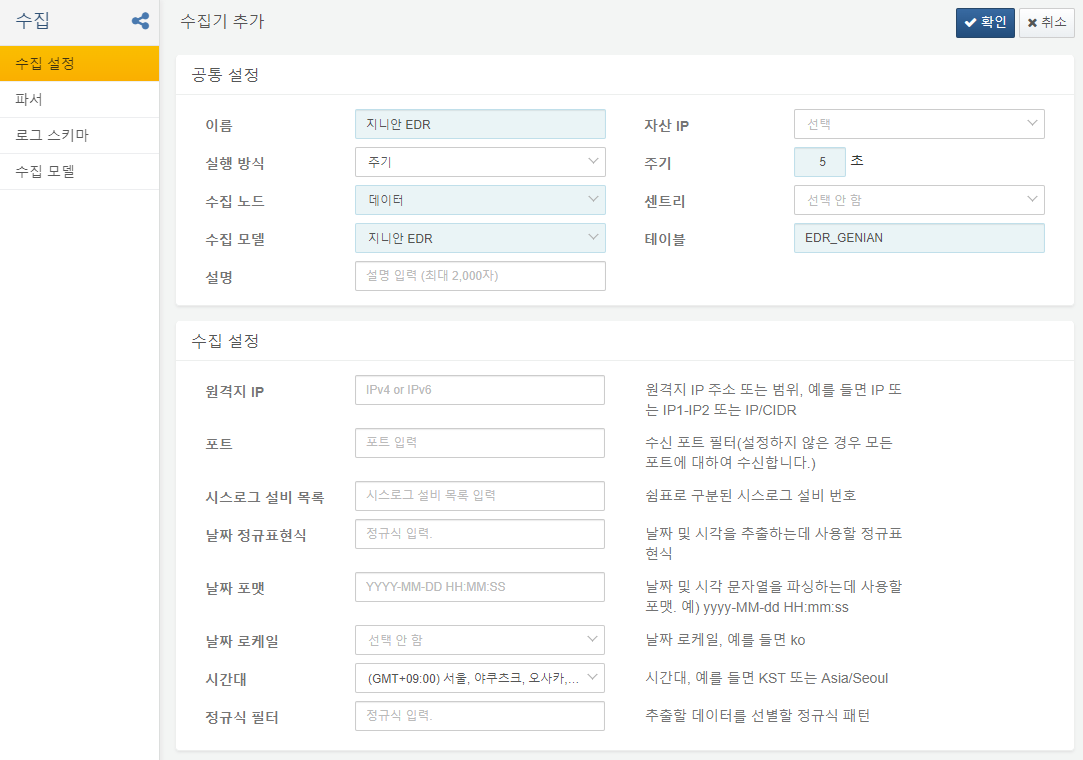
Logger Settings
To add and activate the Genian EDR logger, configure the following settings:
- Logger model: Genian EDR
- Table: EDR_GENIAN (If you rename the table, ensure you update the table name in the dataset as well.)
- Remote IP: The IP address of the Genian EDR server or relay server